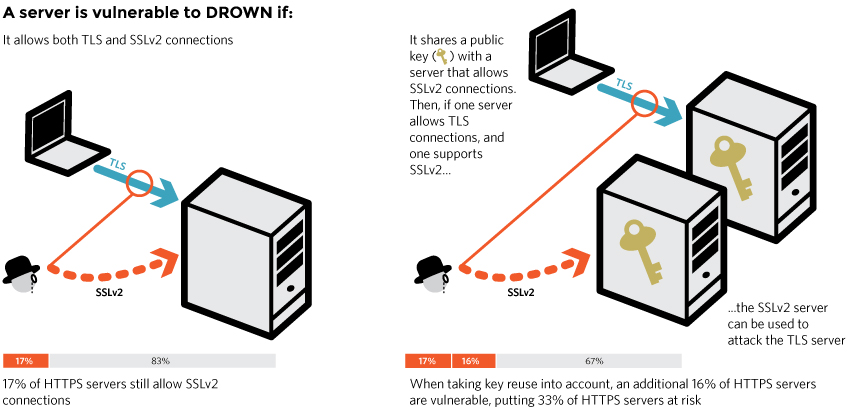
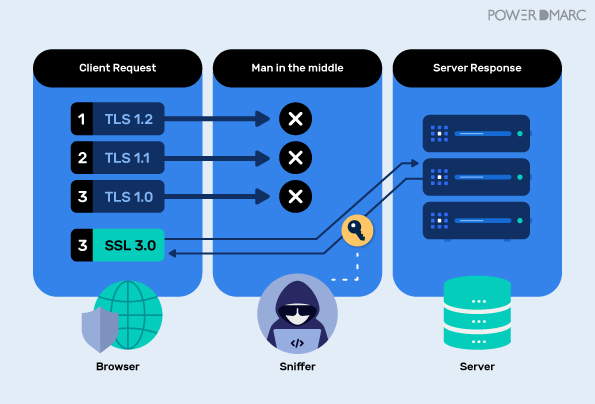
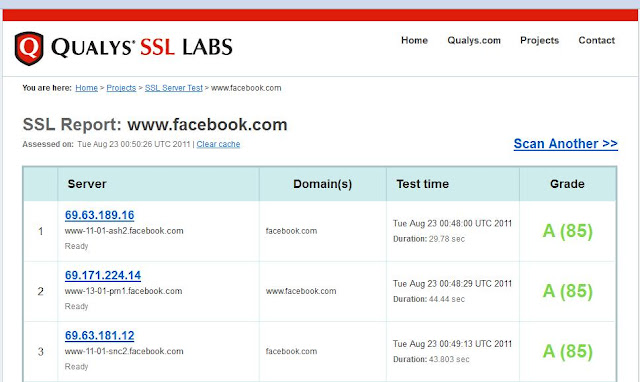
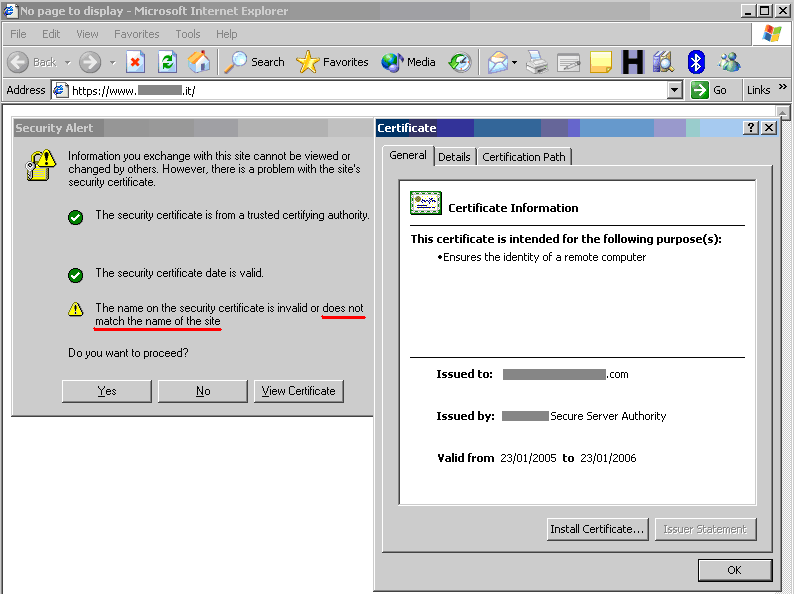
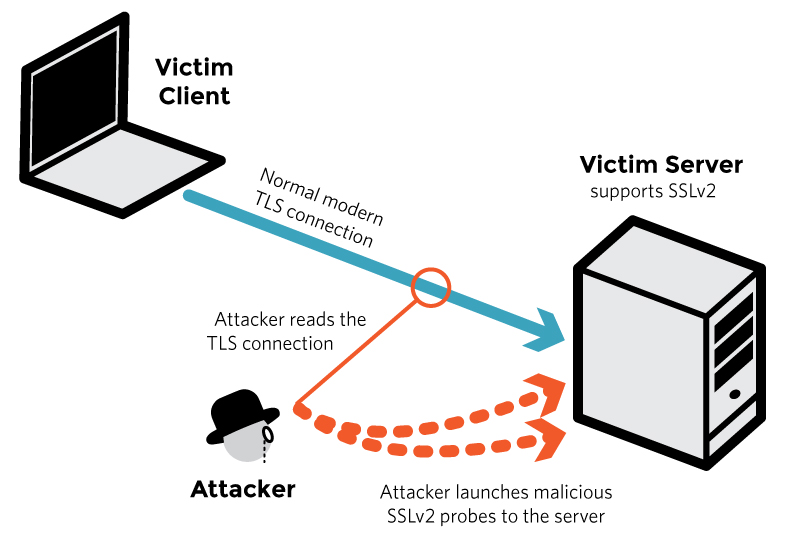
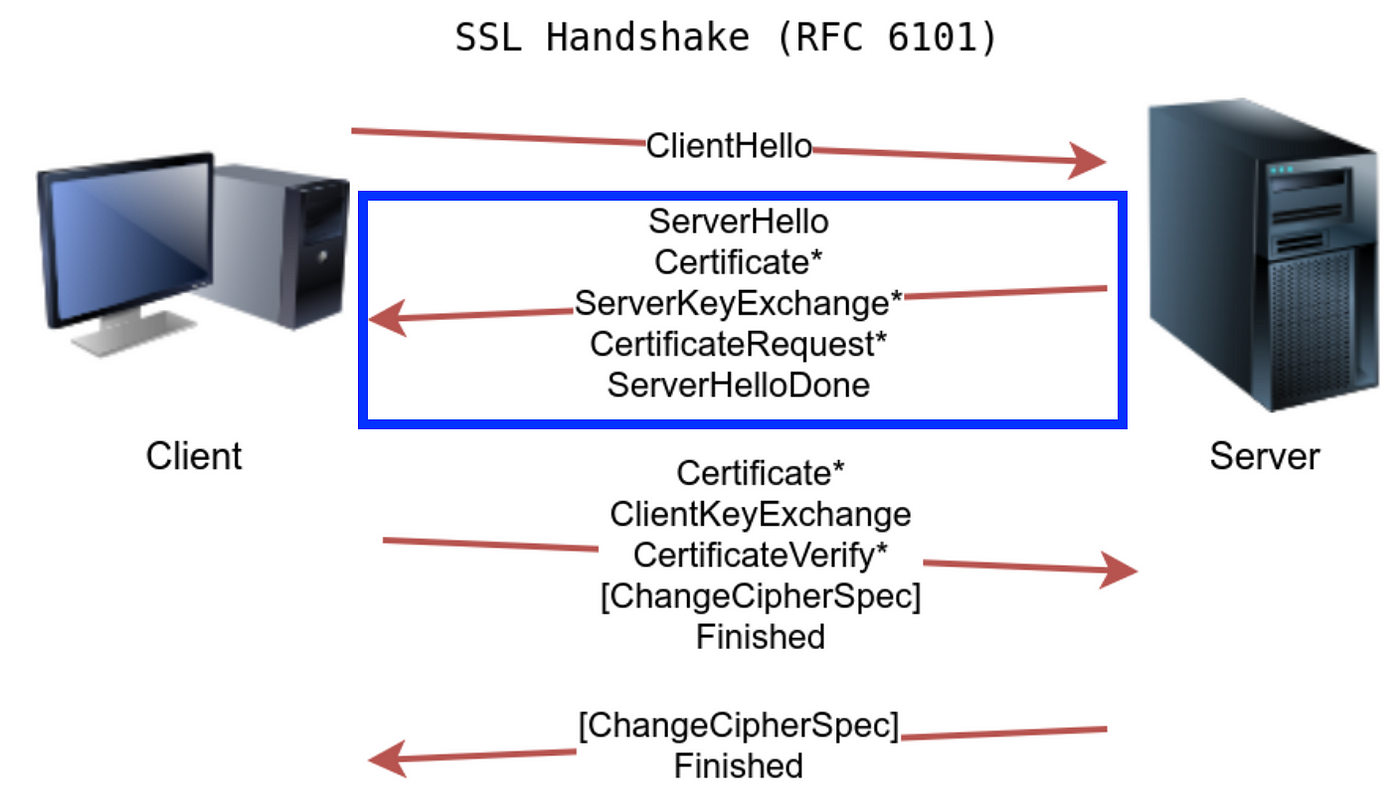
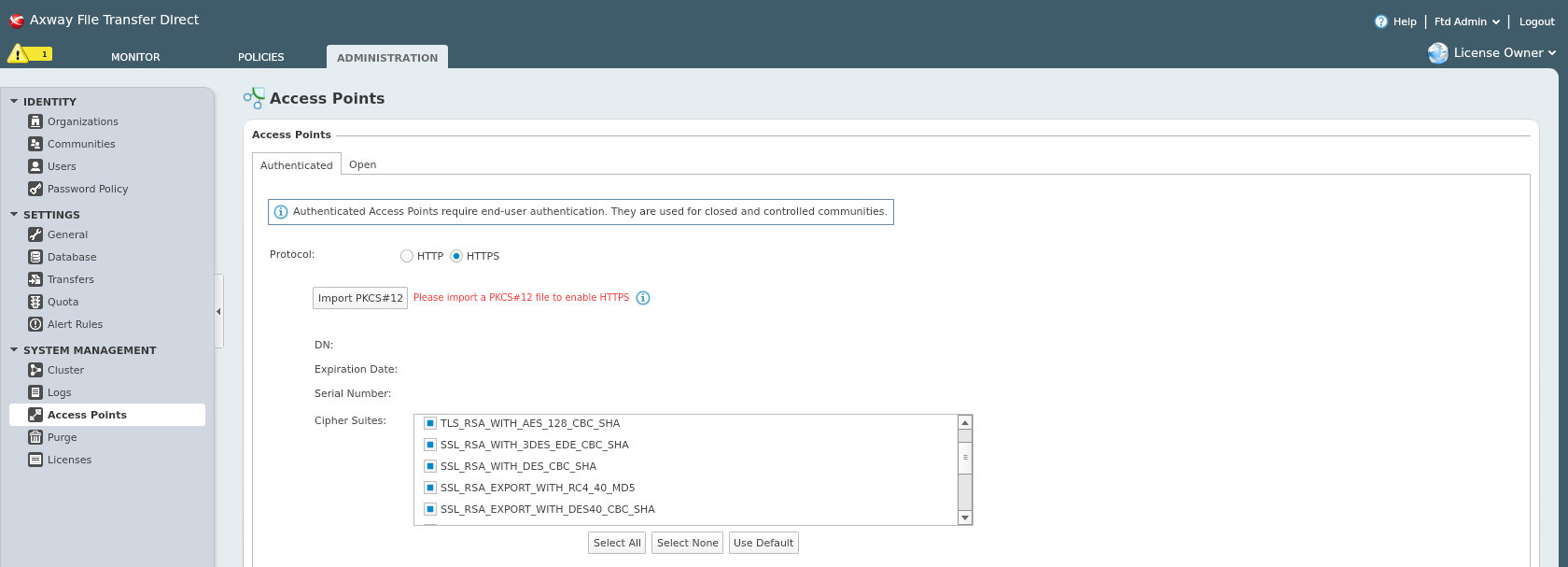
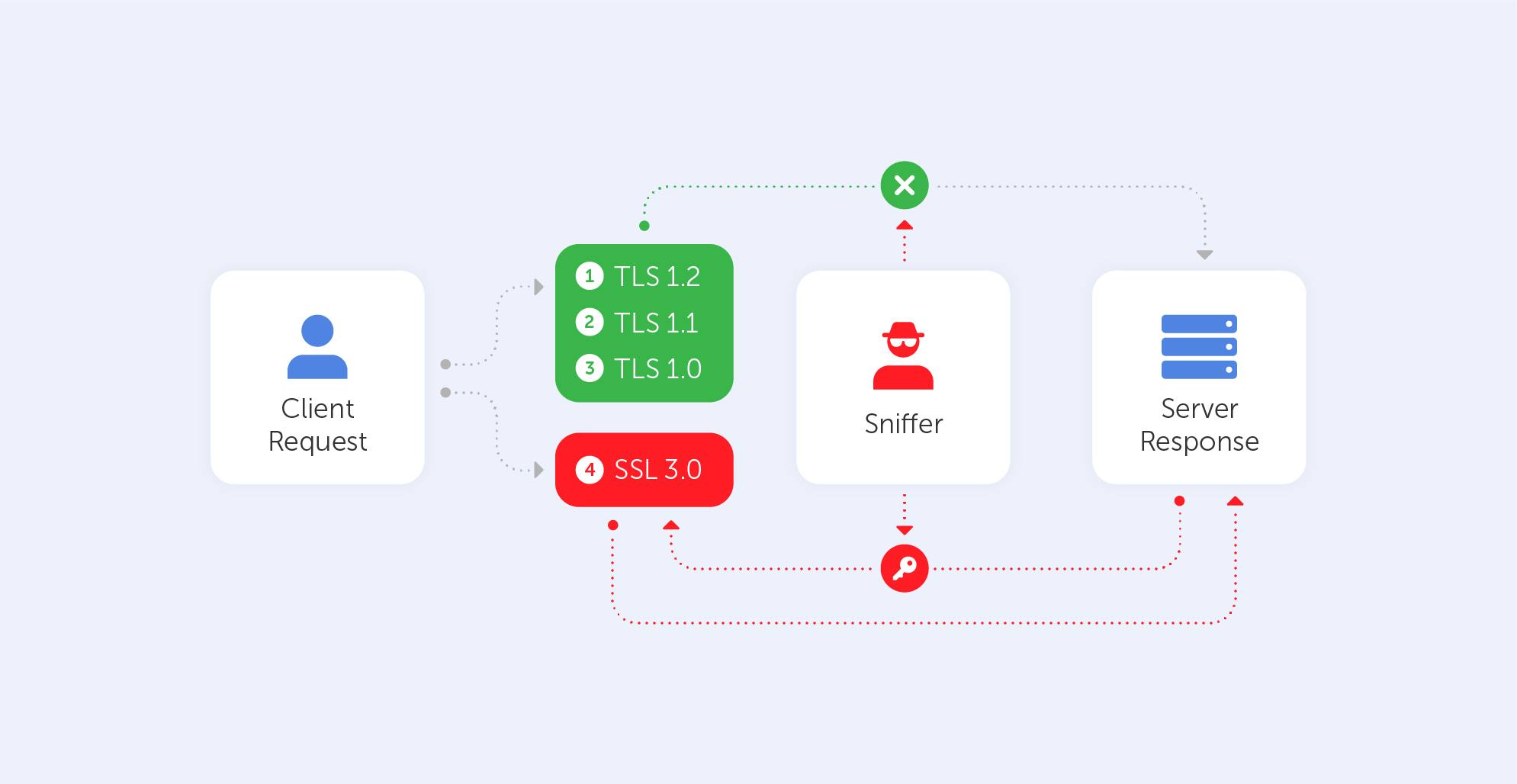
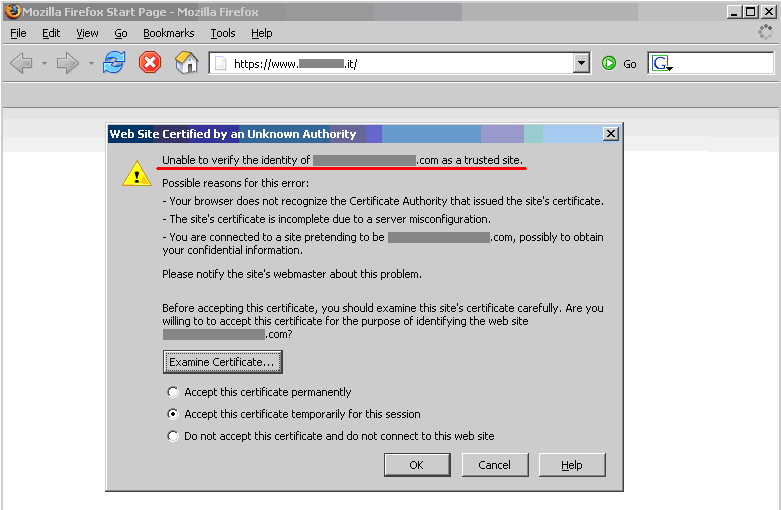
Everything You Need to Know About SSL Stripping attacks & HTTP Strict Transport Secure - DEV Community
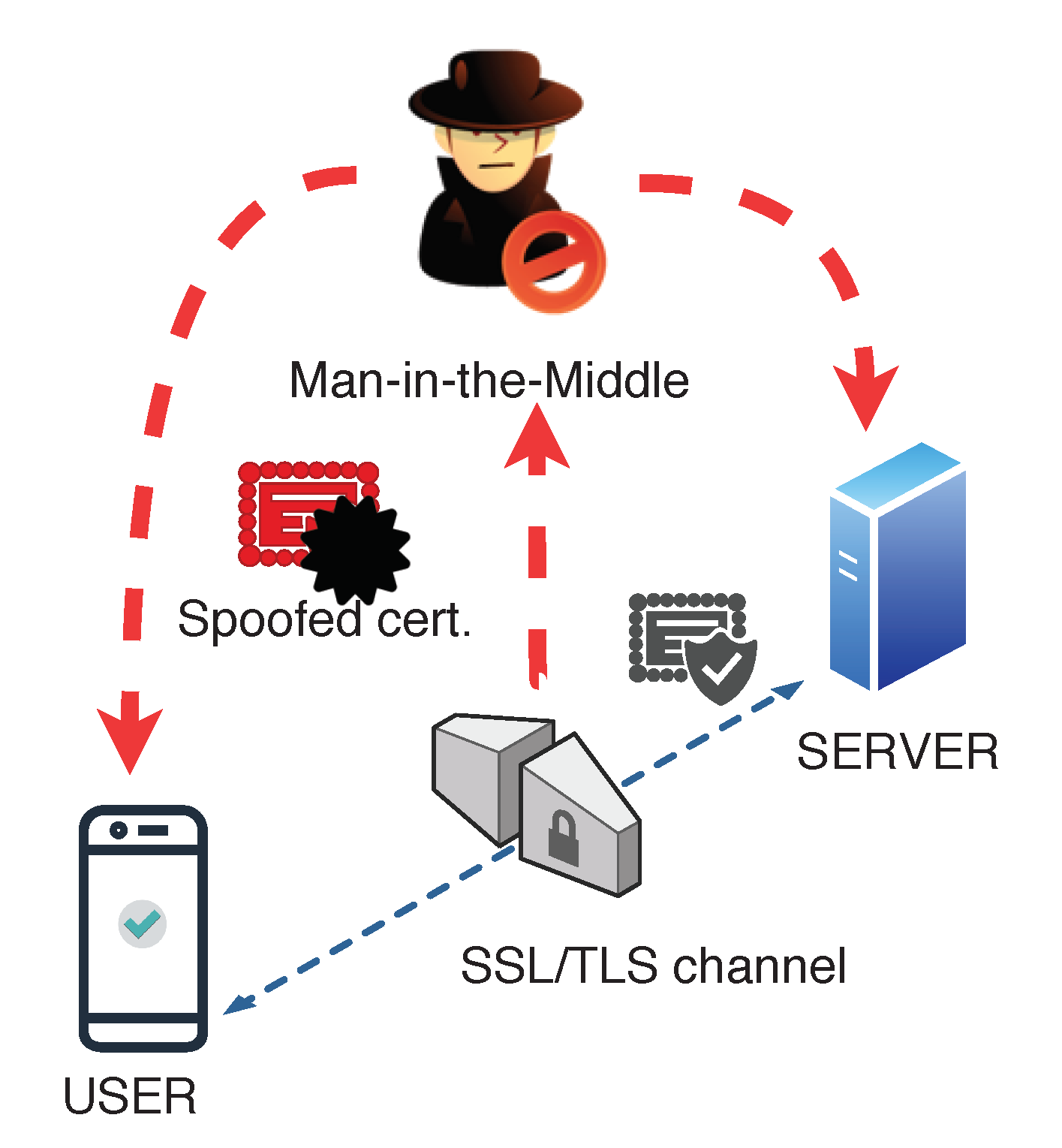
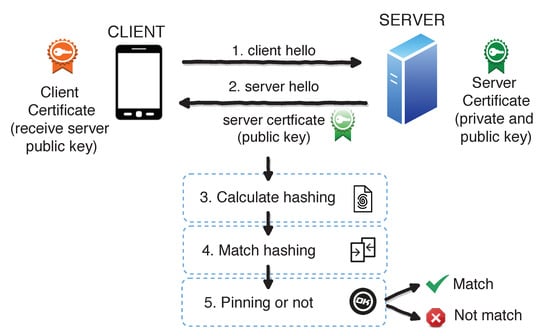
Entropy | Free Full-Text | A Framework to Secure the Development and Auditing of SSL Pinning in Mobile Applications: The Case of Android Devices