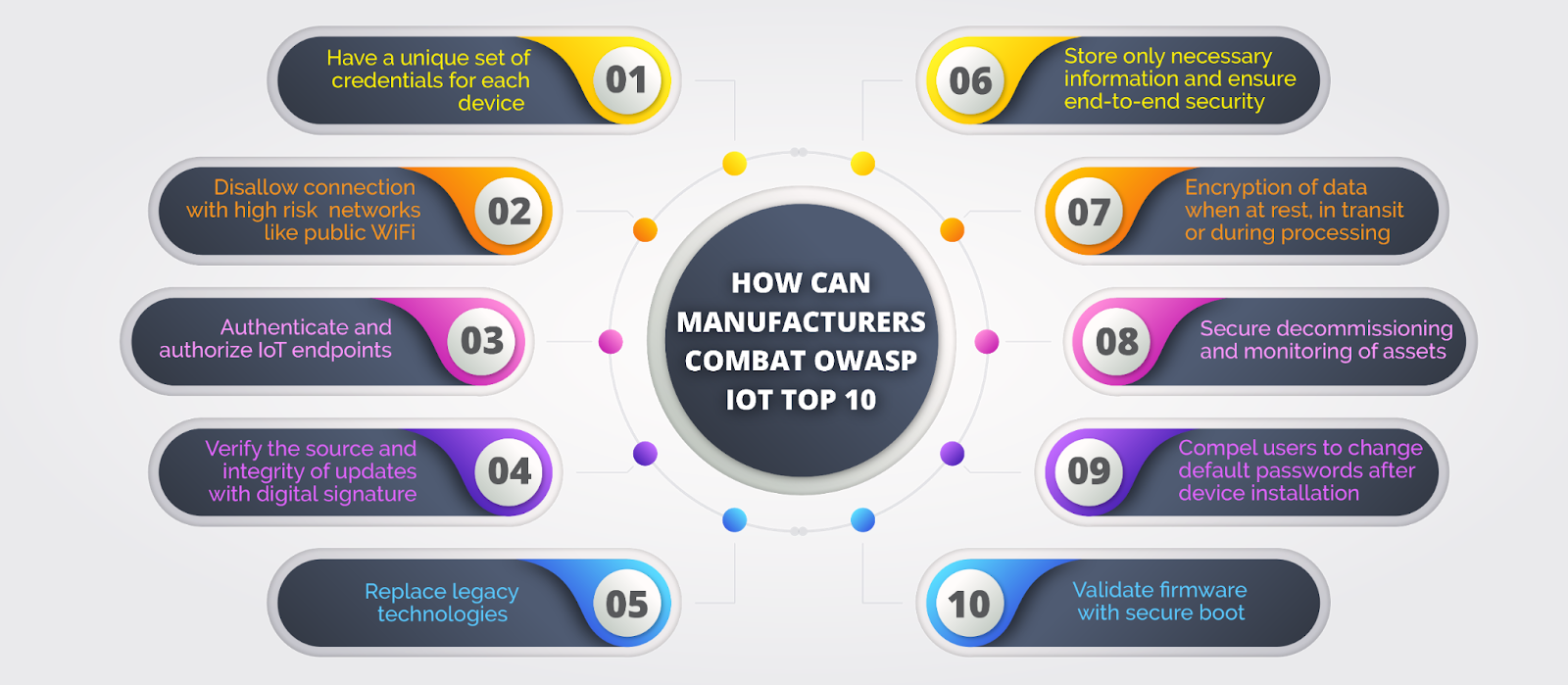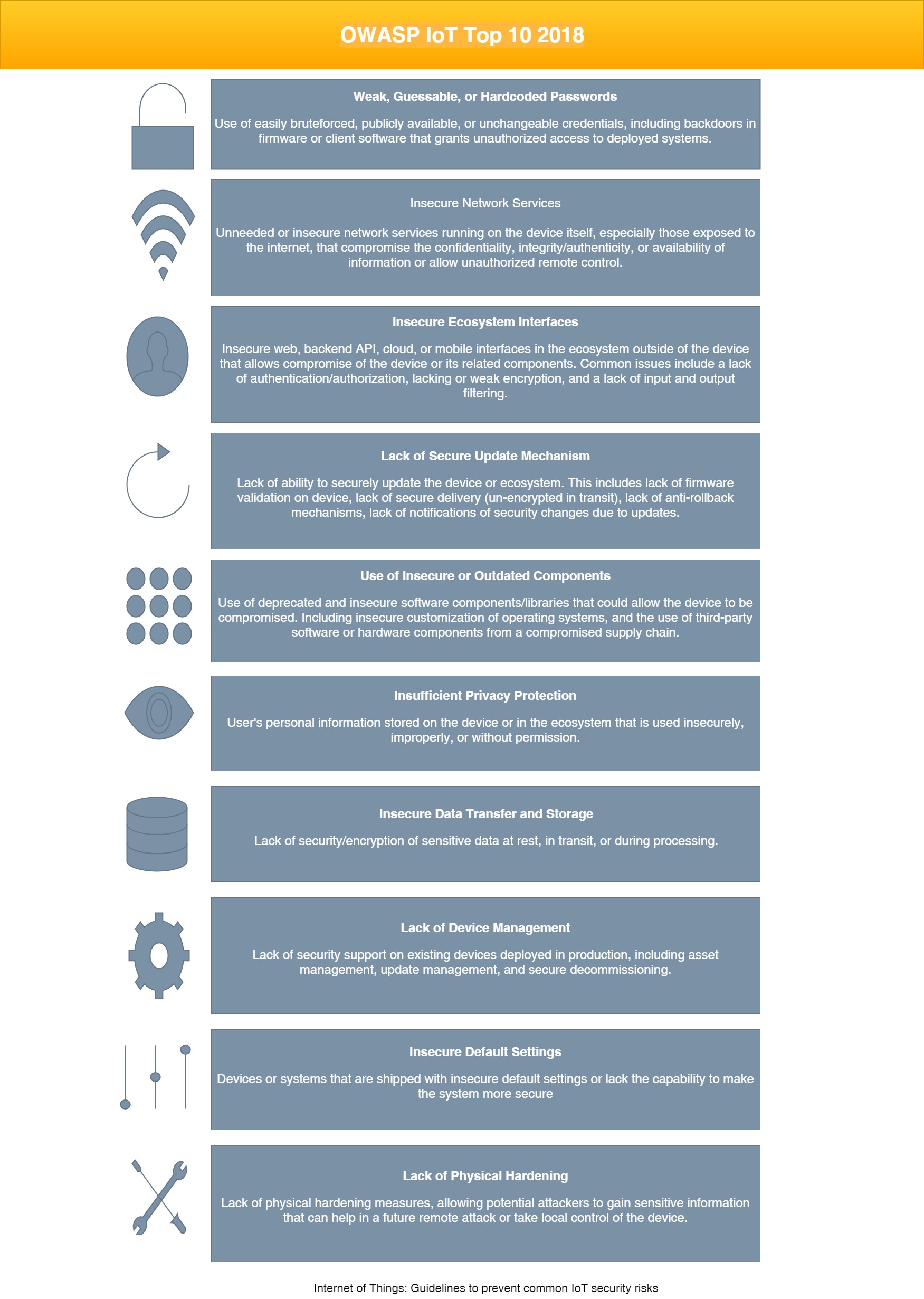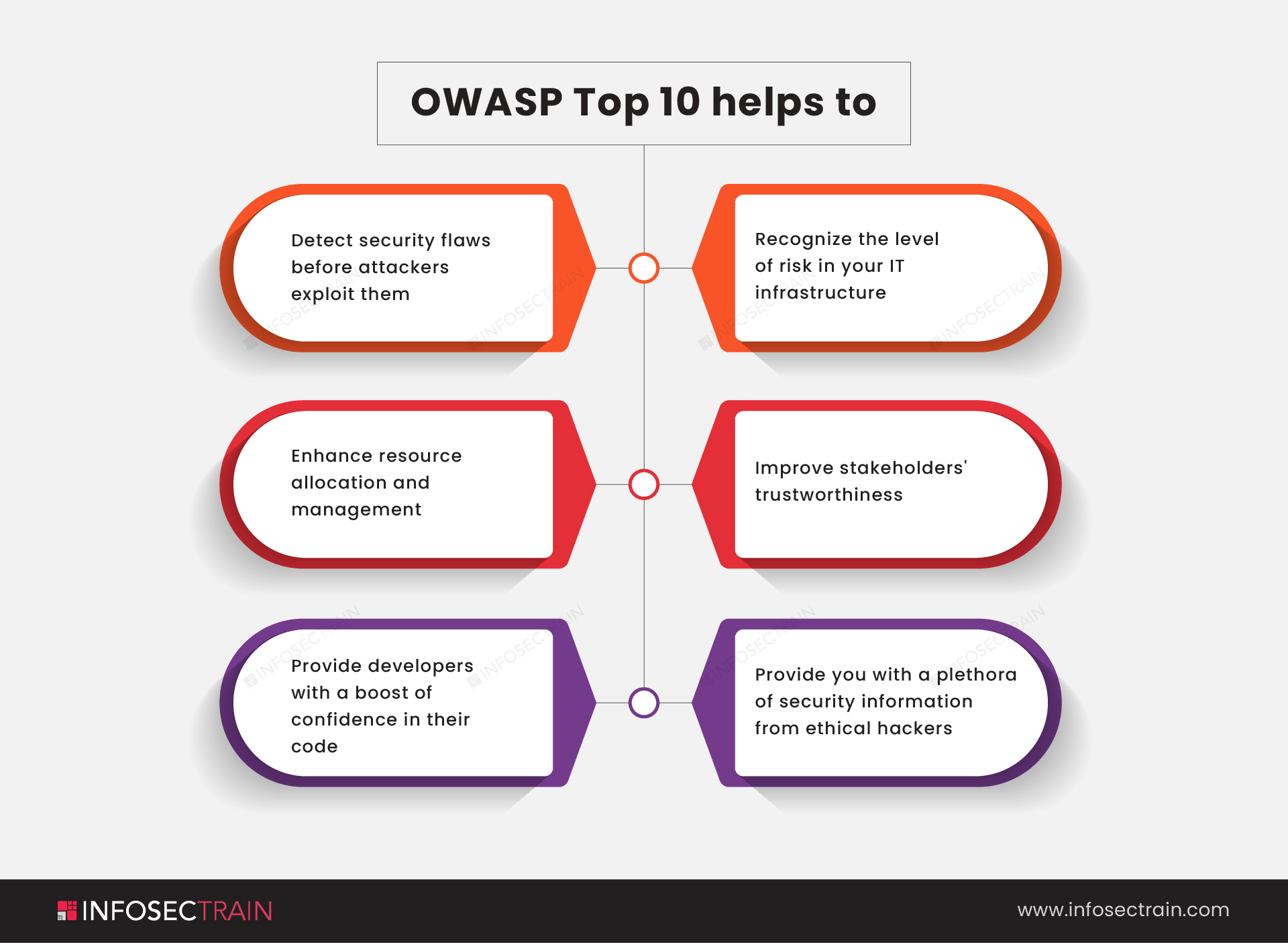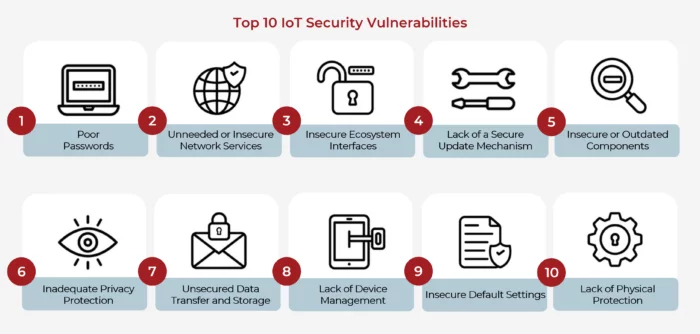
How To Ensure IoT Security in the Face of Vulnerabilities - Contract Engineering, Product Design & Development Company - Cardinal Peak
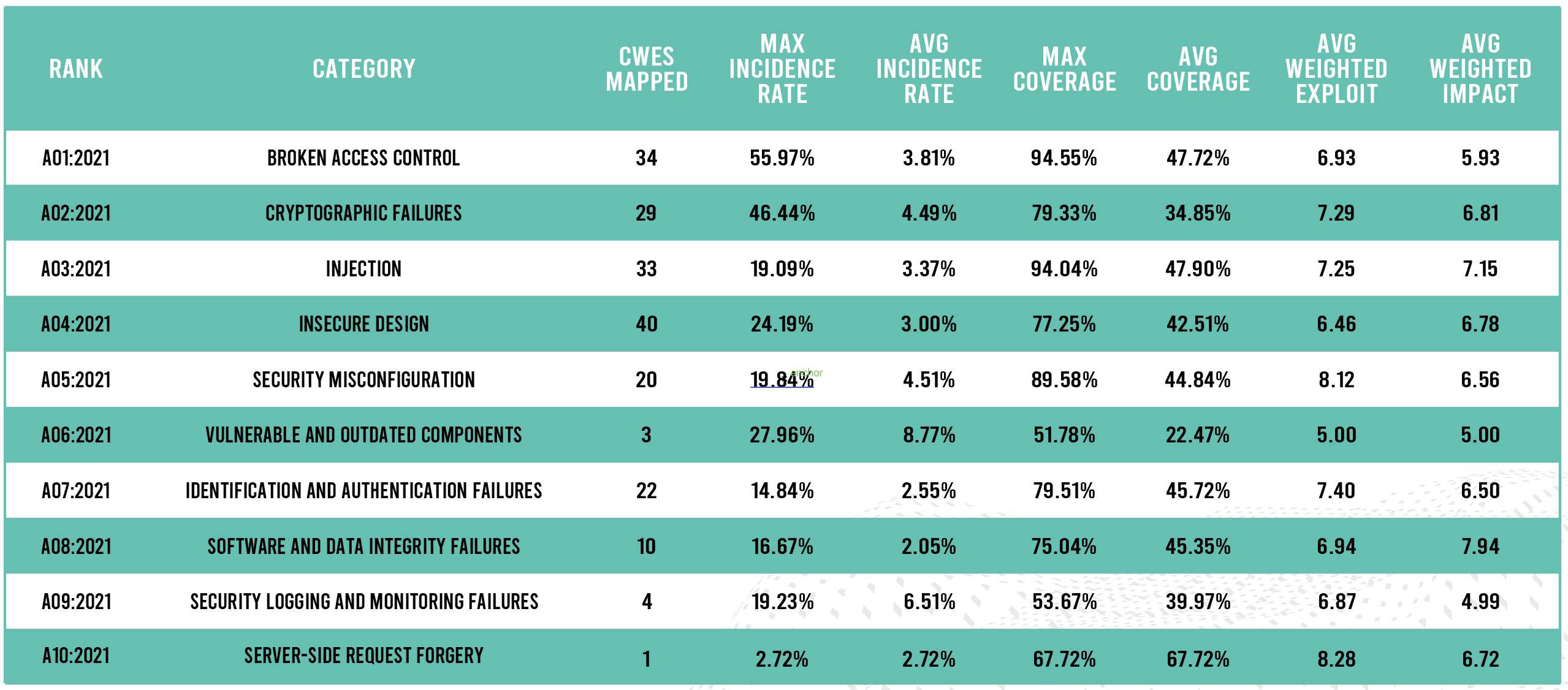
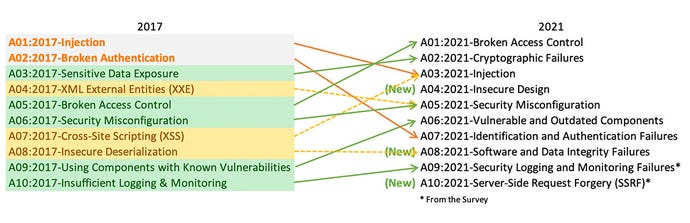
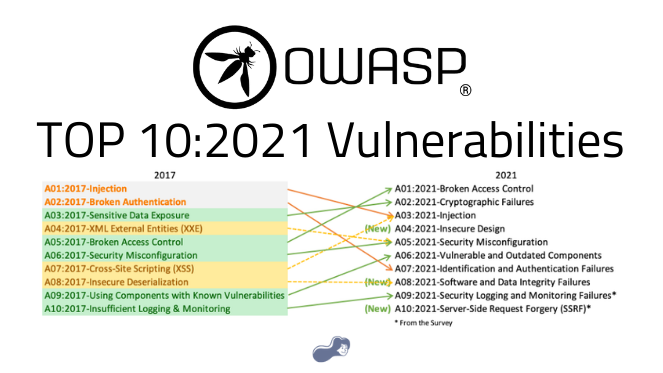
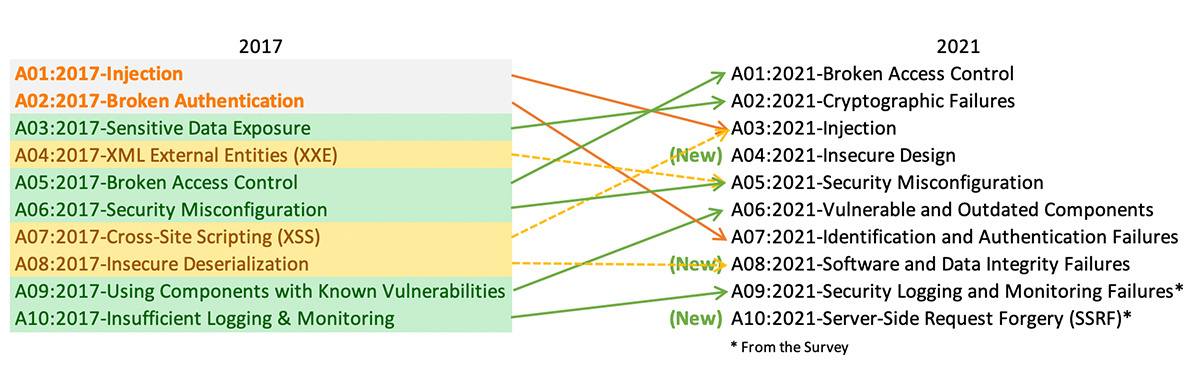
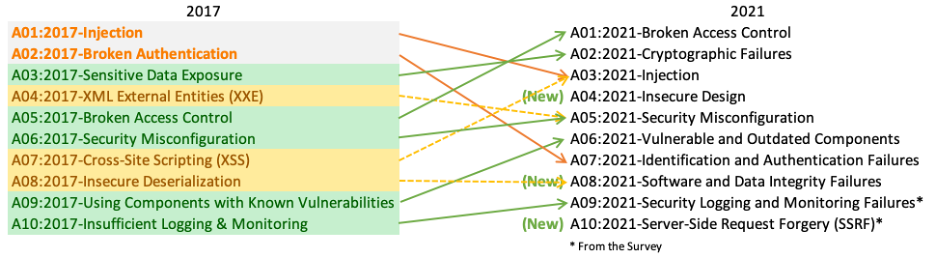
THE 2021 OWASP TOP TEN EMPHASIZES SECURITY CONTROL AREAS OVER INDIVIDUAL VULNERABILITIES FOR IMPROVED RISK MANAGEMENT - Security Boulevard