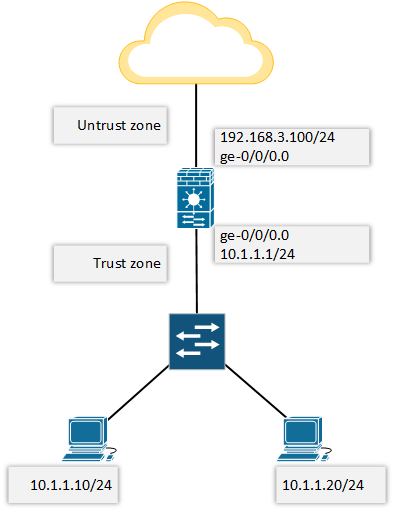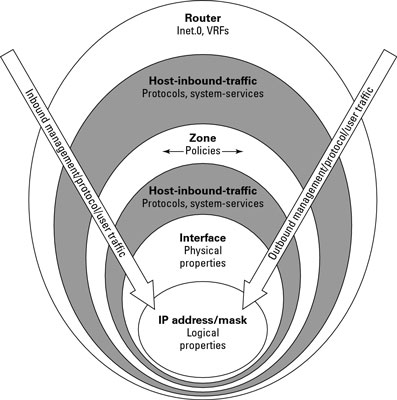
Juniper : Introduction to the Junos Operating System: How to Configure SRX Security Zones with Junos
Baseline security requirements for network security zones (version 2.0) - ITSP.80.022 - Canadian Centre for Cyber Security
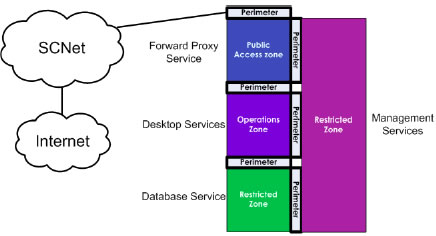
Network security zoning - Design considerations for placement of services within zones (ITSG-38) - Canadian Centre for Cyber Security