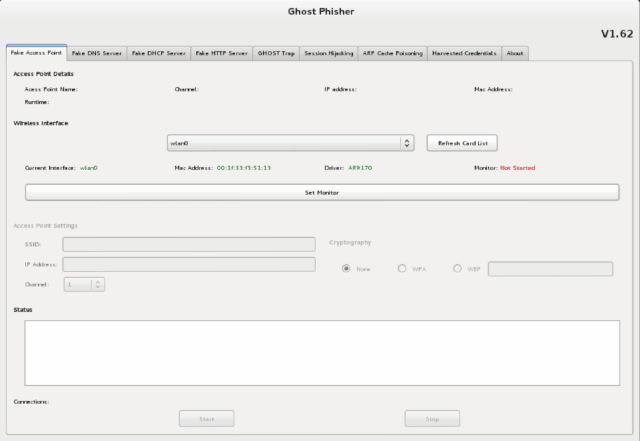
Ghost Phisher - Phishing Attack Tool With GUI - Darknet - Hacking Tools, Hacker News & Cyber Security
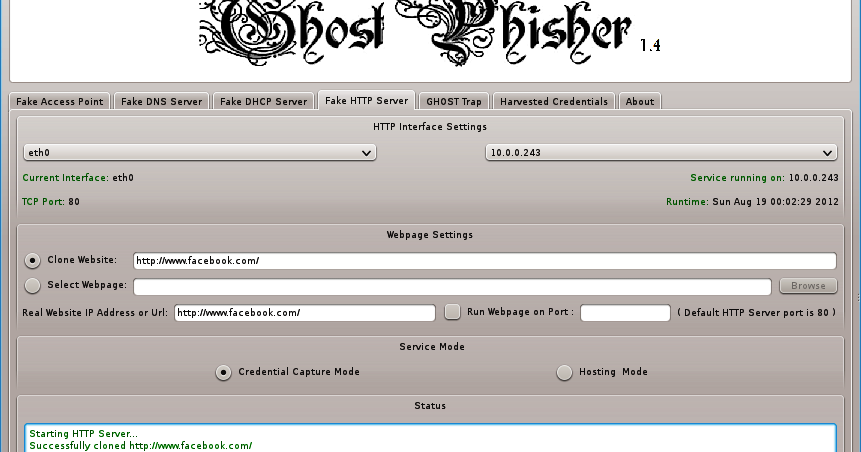
How Hackers Still Manage to Steal Facebook Passwords: How You Can Protect Yourself – The Cybersecurity Man
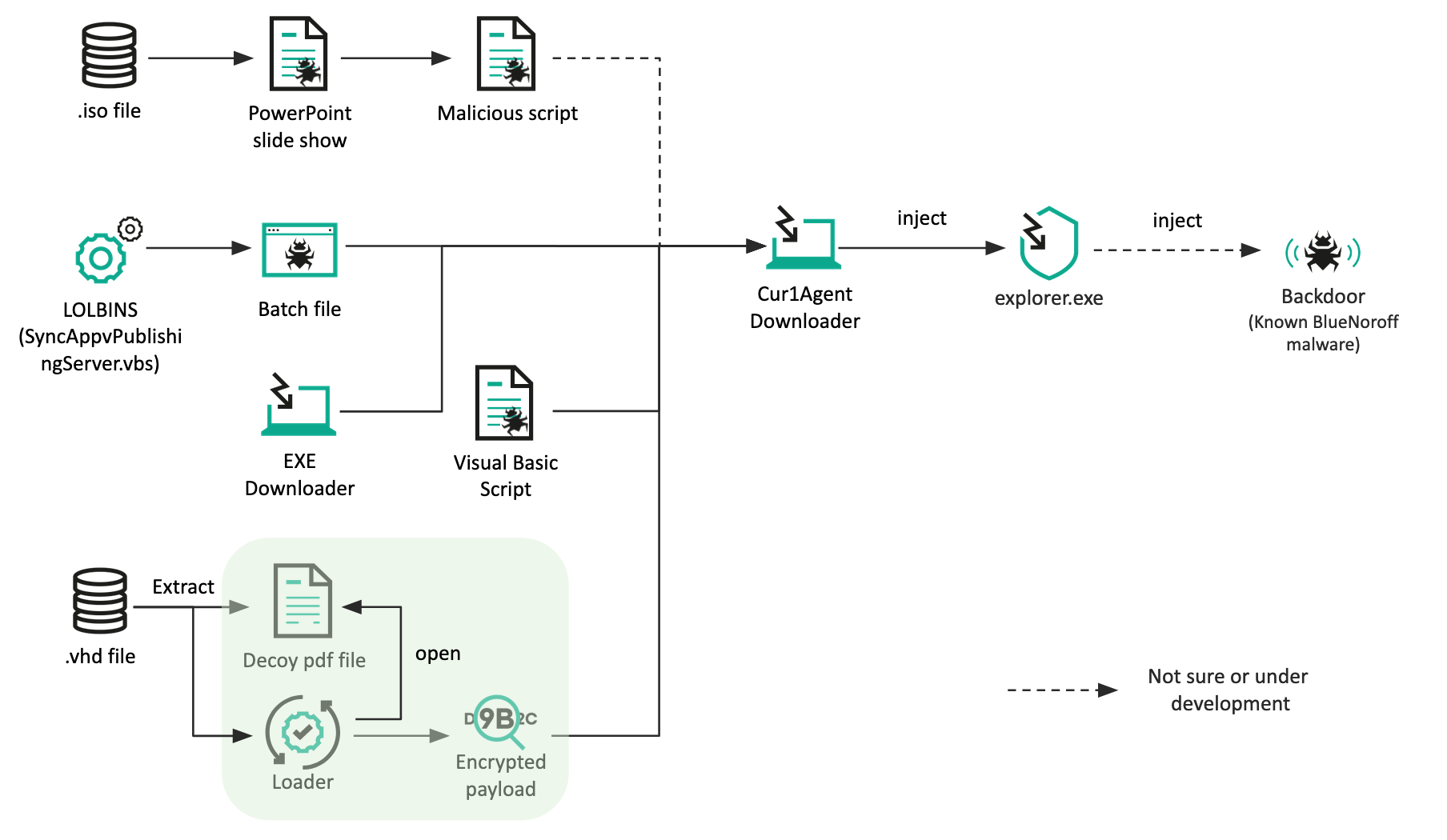
![Working with Ghost Phisher - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book] Working with Ghost Phisher - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781789340563/files/assets/ac92bcf9-e402-4065-8e0a-39db8406c55f.png)
Working with Ghost Phisher - Mastering Kali Linux for Advanced Penetration Testing - Third Edition [Book]
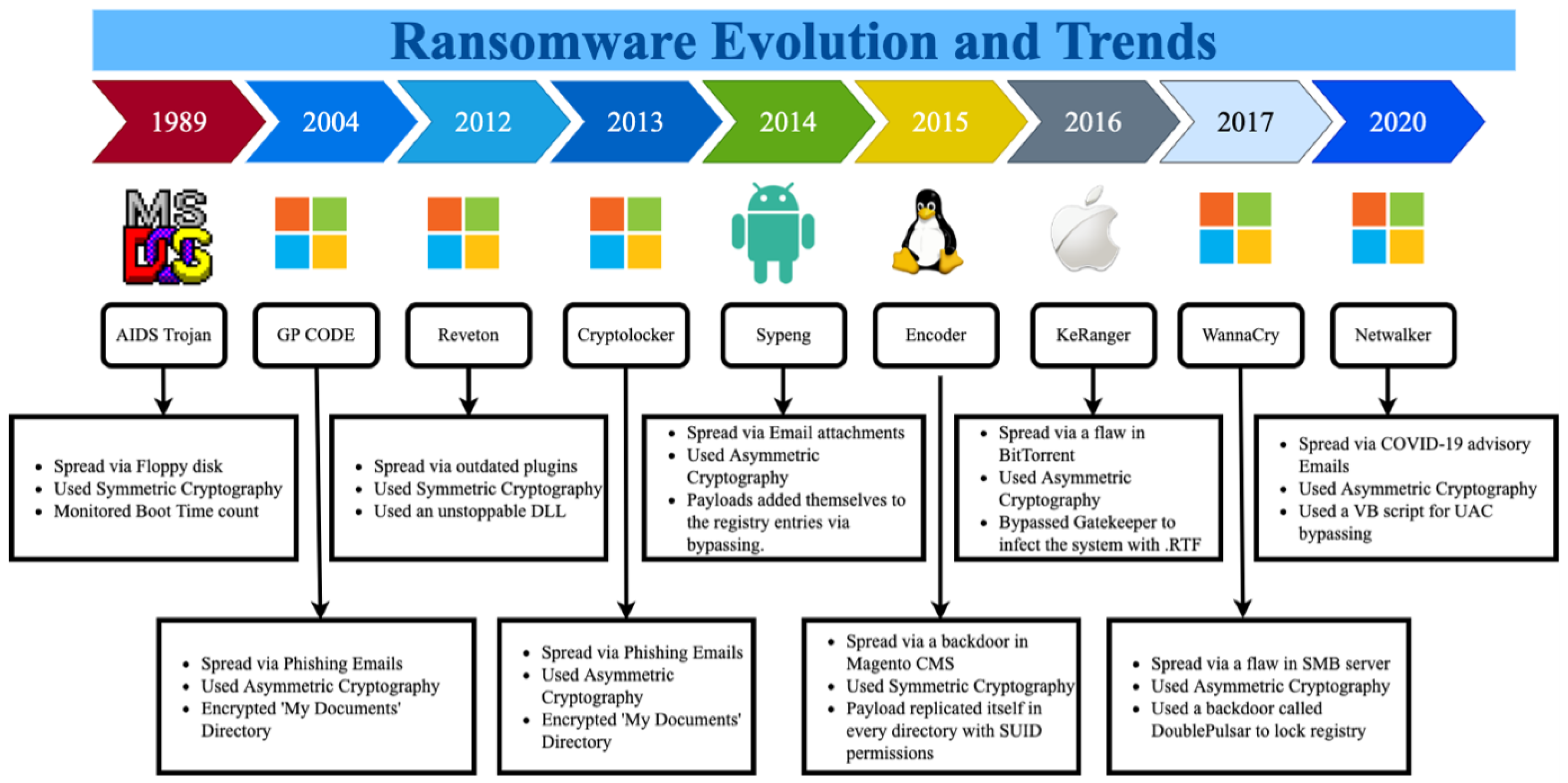
Sustainability | Free Full-Text | Ransomware Detection, Avoidance, and Mitigation Scheme: A Review and Future Directions









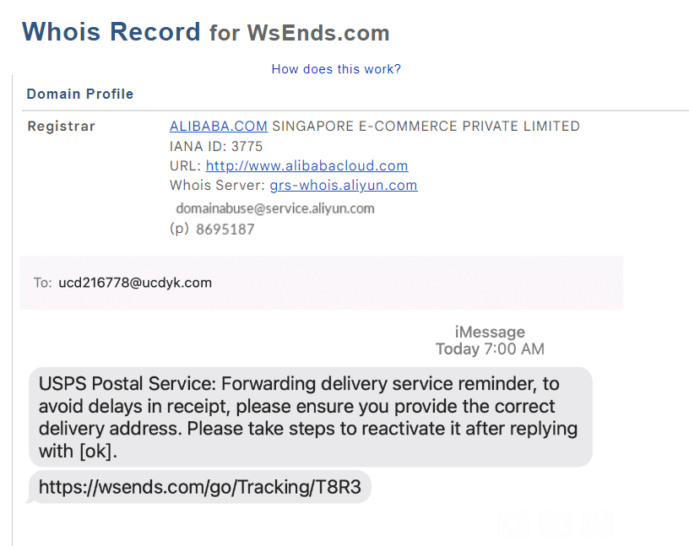


![How to do it... - Kali Linux - An Ethical Hacker's Cookbook [Book] How to do it... - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/5de7687f-5874-4b4e-b824-7421144c0eb5.png)

