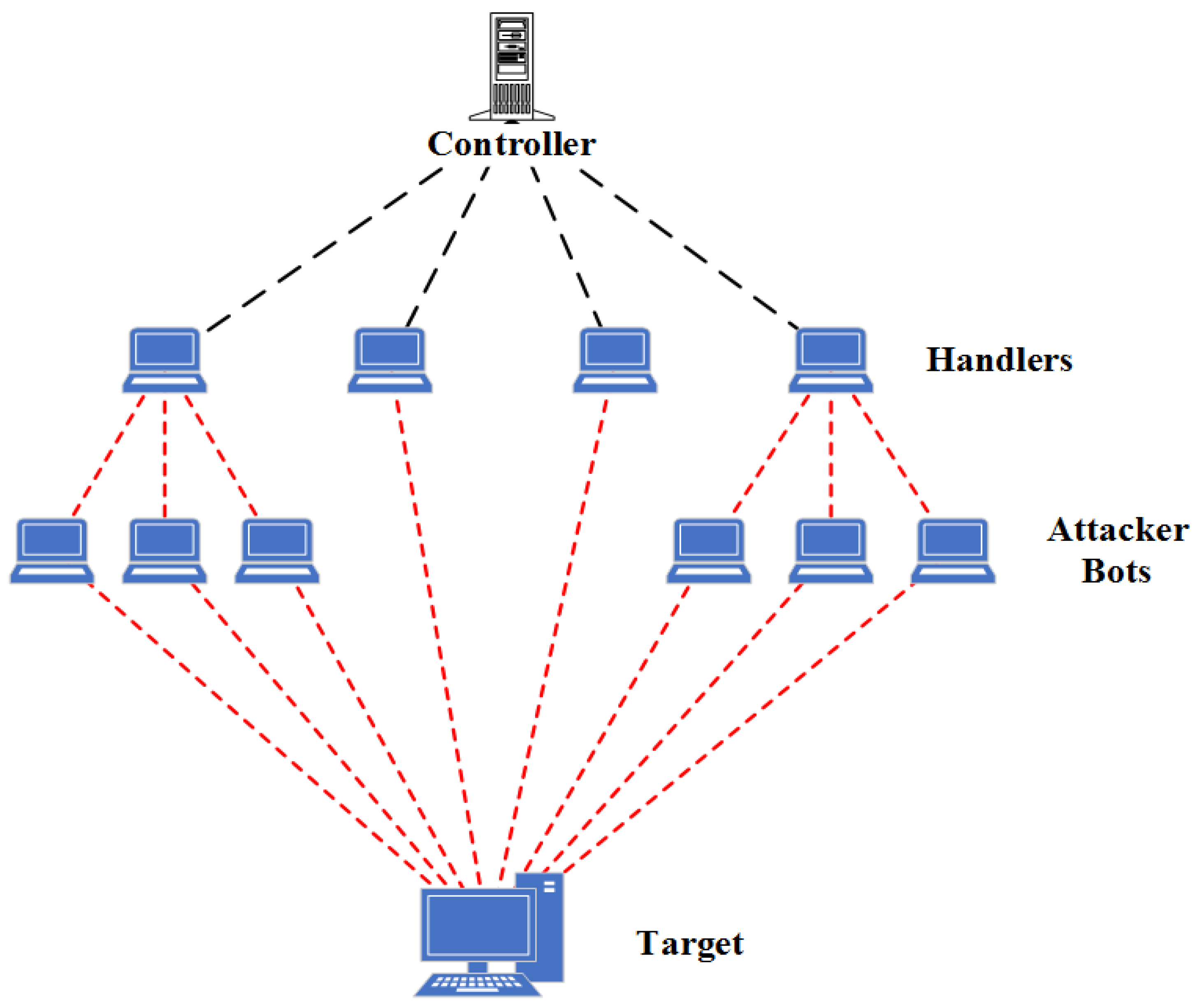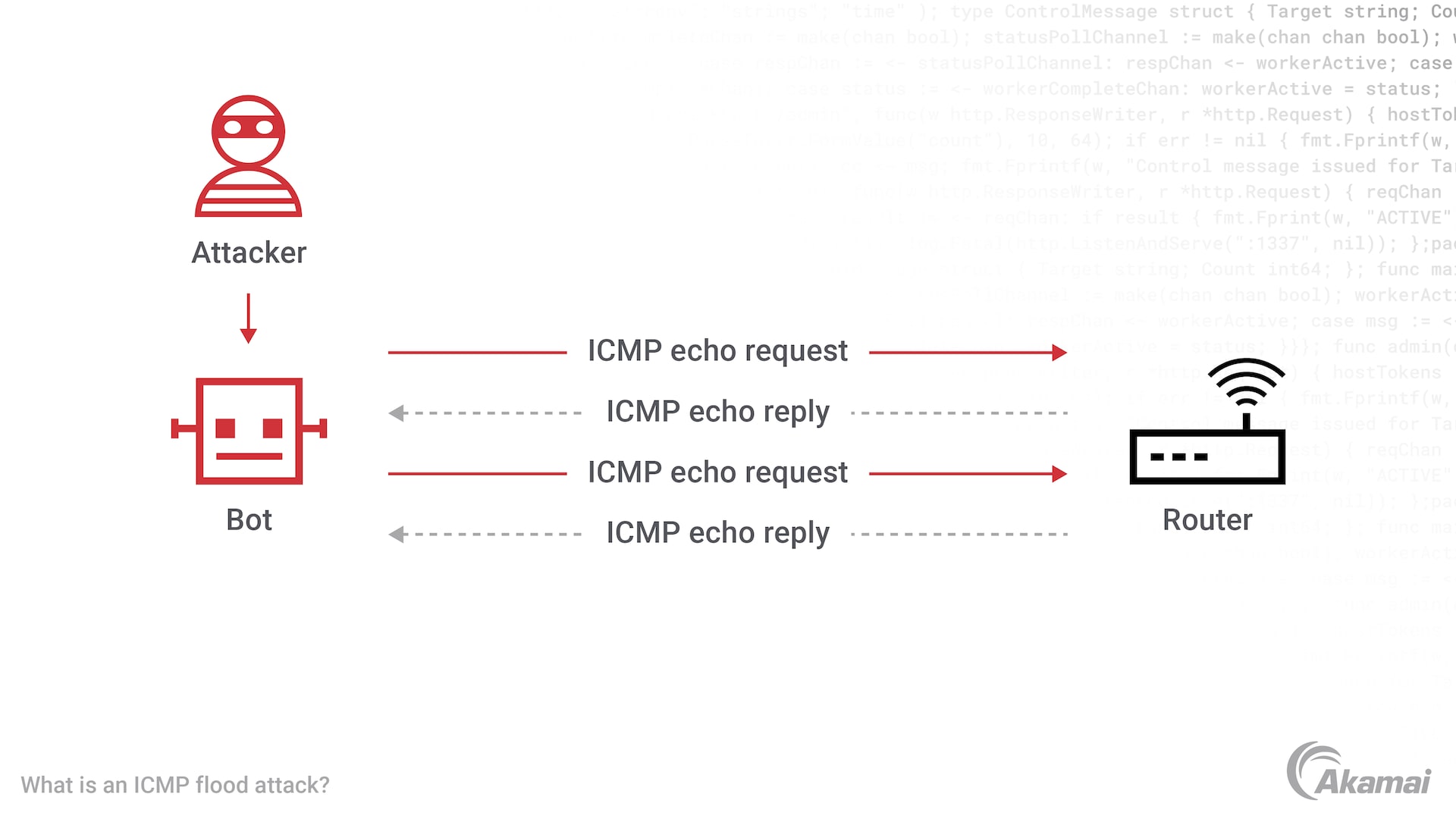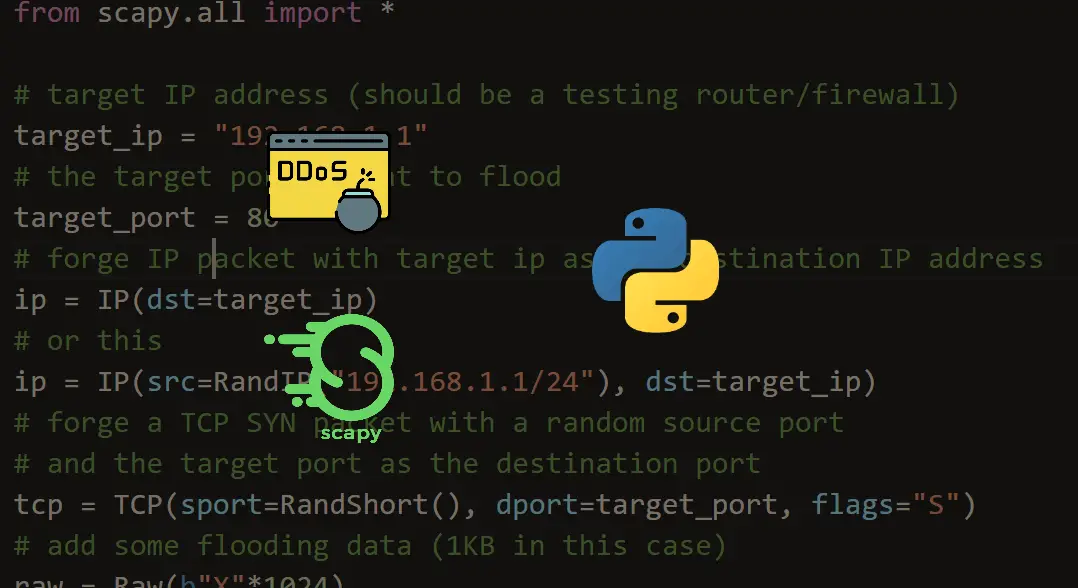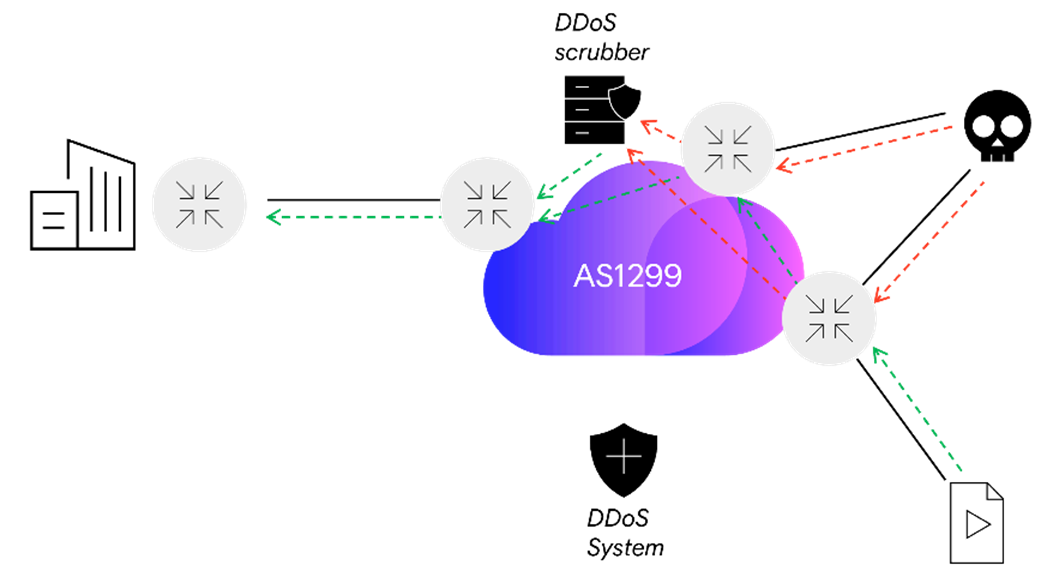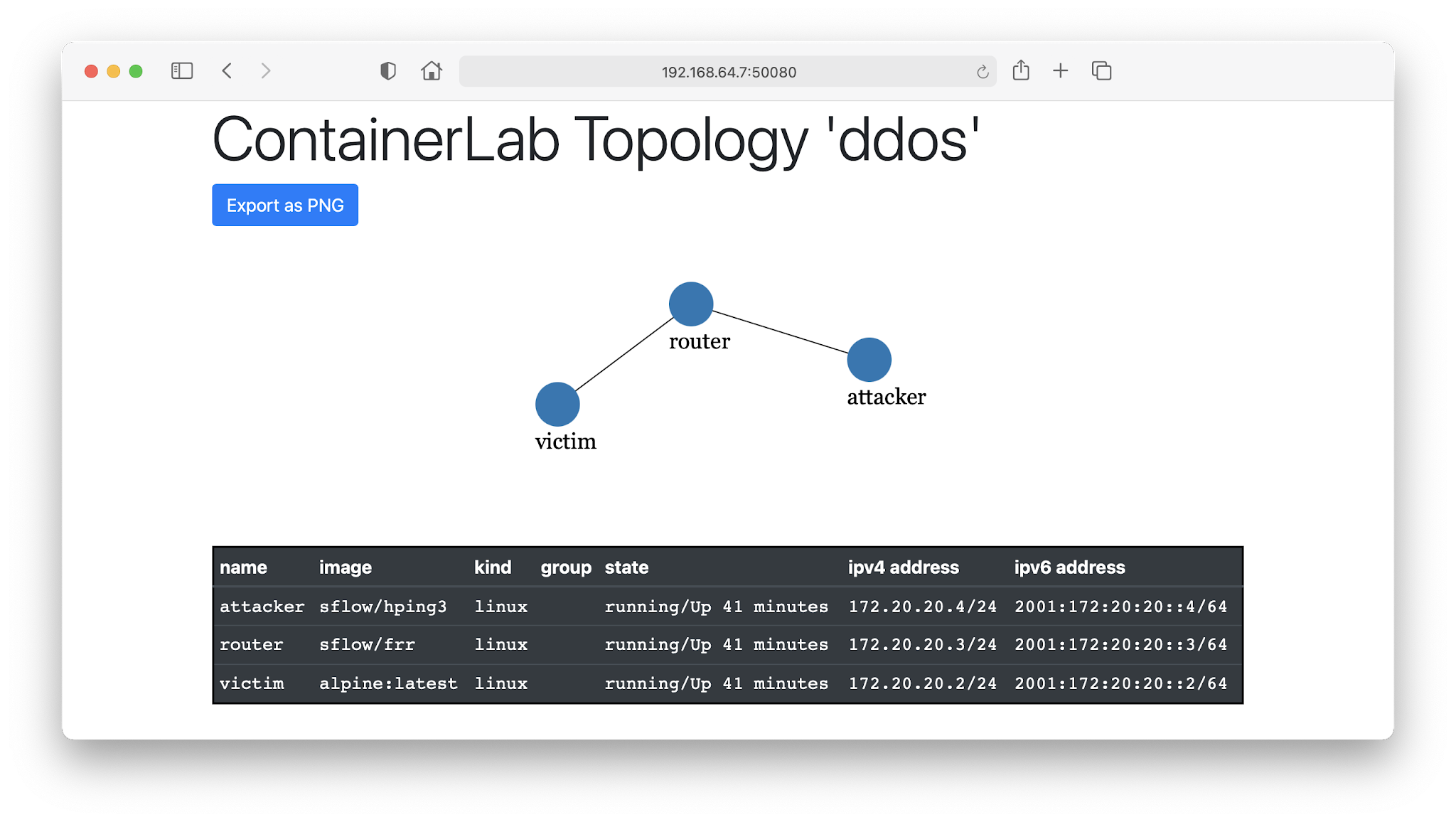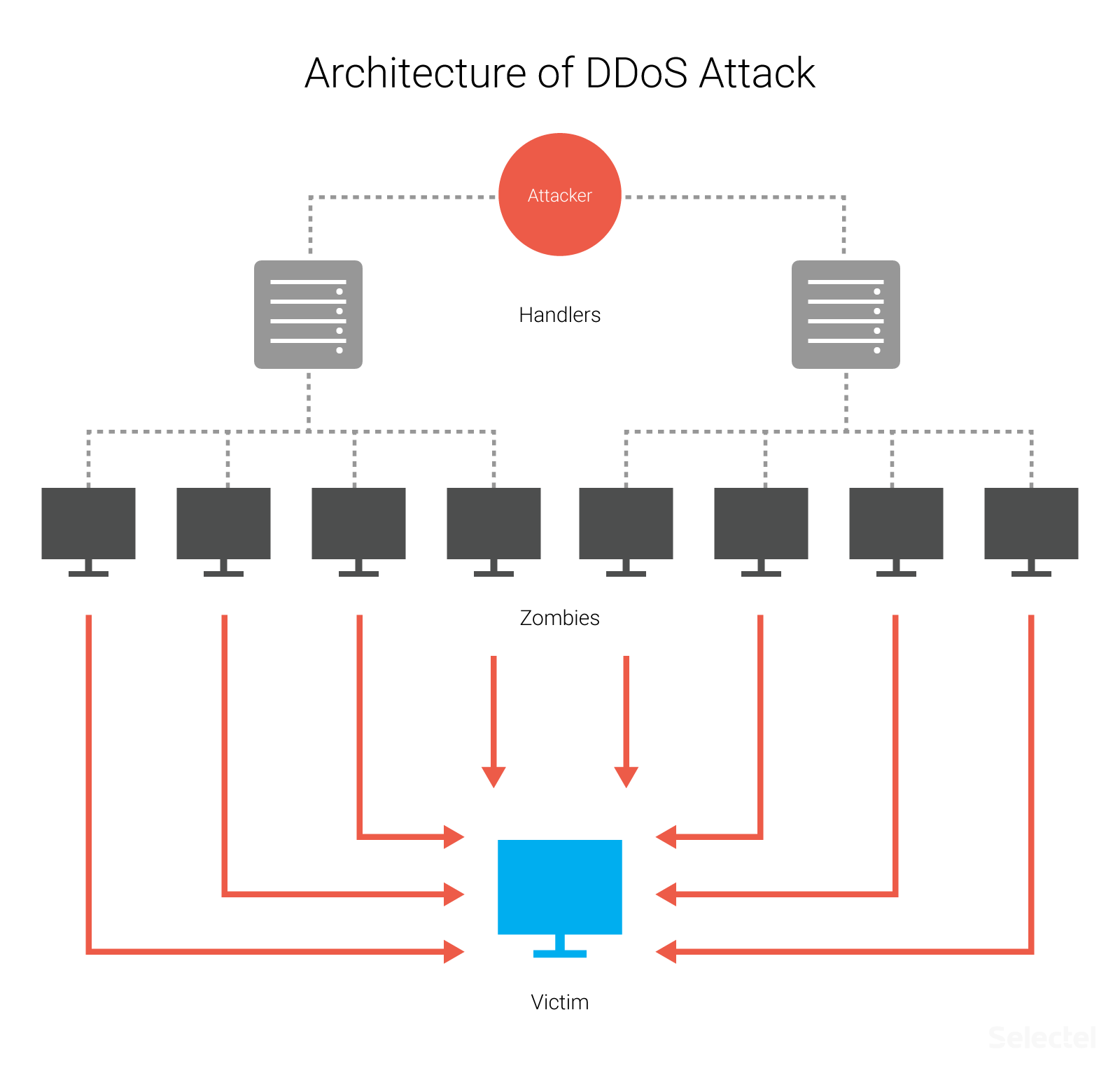
DDOS Attack Types and Mitigation Strategies | New Jersey Cybersecurity & Communications Integration Cell

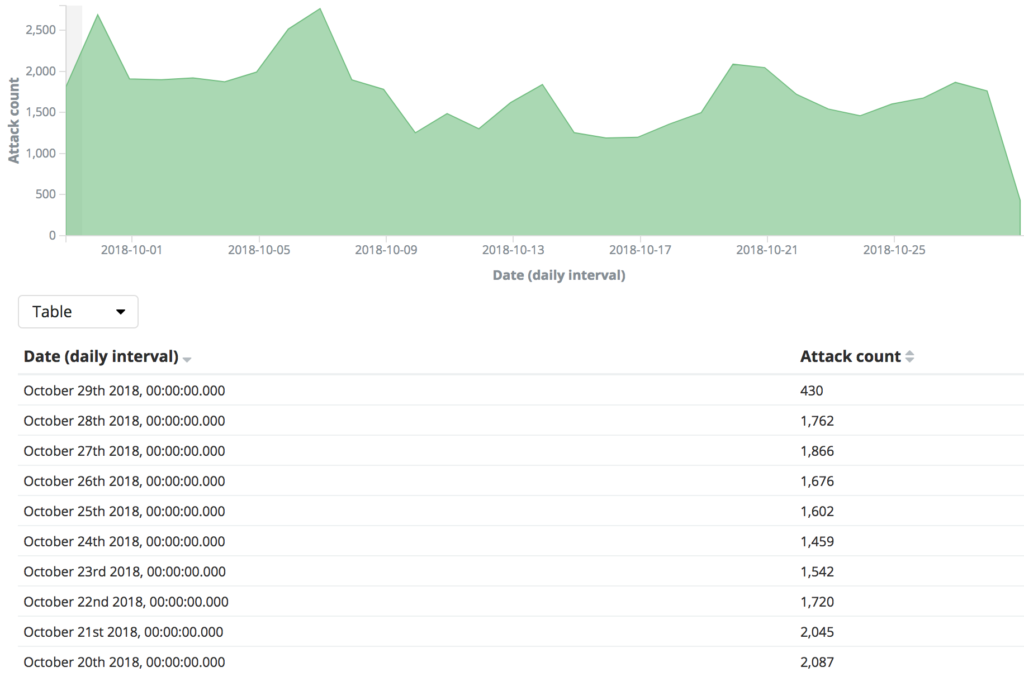
2017 DDoS and Web Application Attack Landscape - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

Amazon.com: TP-Link ER605 V2 Wired Gigabit VPN Router | Up to 3 WAN Ethernet Ports + 1 USB WAN | SPI Firewall SMB Router | Omada SDN Integrated | Load Balance | Lightning Protection : Electronics
![Application Hosting Configuration Guide for Cisco NCS 540 Series Routers - Cisco Secure DDoS Edge Protection [Cisco Network Convergence System 540 Series Routers] - Cisco Application Hosting Configuration Guide for Cisco NCS 540 Series Routers - Cisco Secure DDoS Edge Protection [Cisco Network Convergence System 540 Series Routers] - Cisco](https://www.cisco.com/content/dam/en/us/td/i/400001-500000/470001-480000/475001-476000/475325.jpg)
Application Hosting Configuration Guide for Cisco NCS 540 Series Routers - Cisco Secure DDoS Edge Protection [Cisco Network Convergence System 540 Series Routers] - Cisco
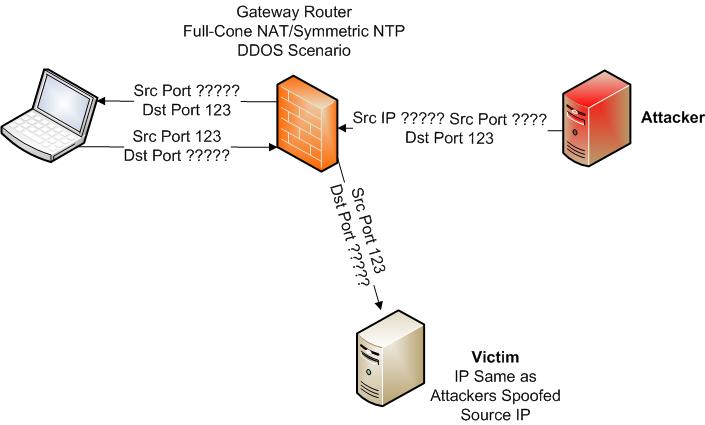
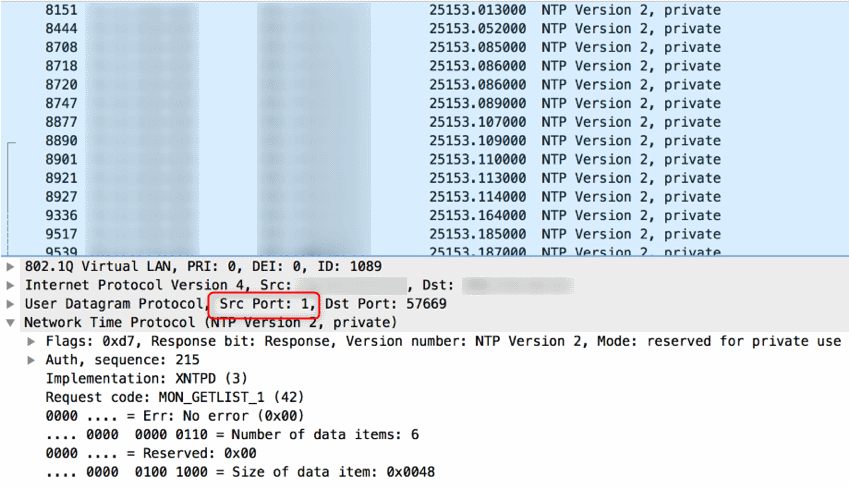
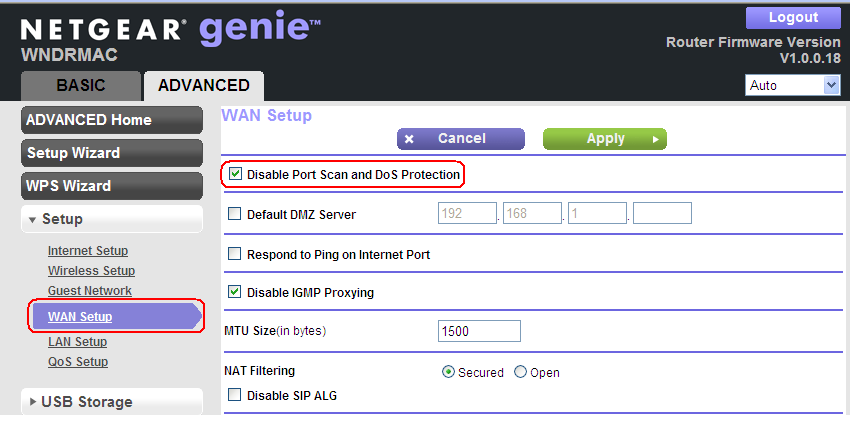
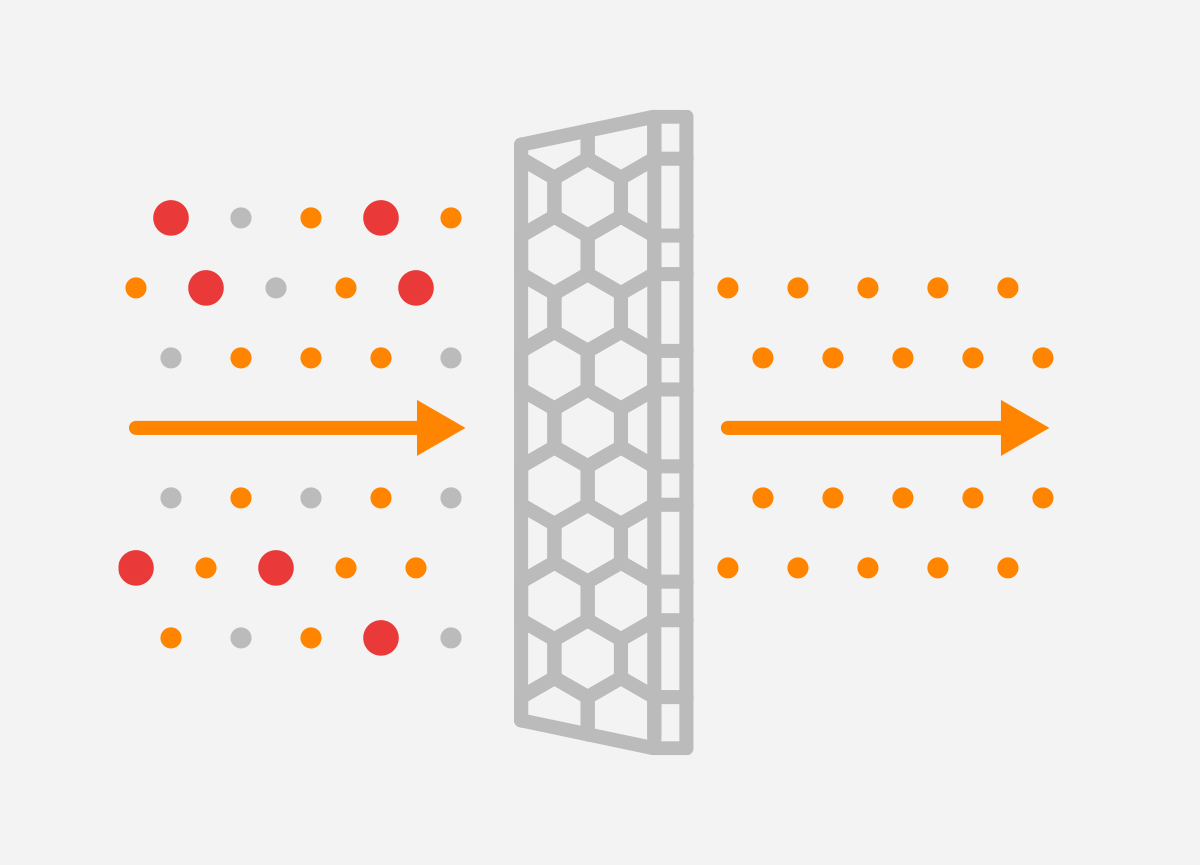
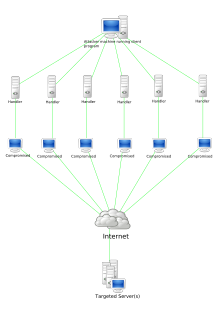
Part 2: Is your home network unwittingly contributing to NTP DDOS attacks? - SANS Internet Storm Center